Human factors that influence secure software development
Dr. Anita D’Amico and Chris Horn gave a well-received presentation about the Human factors that influence secure software development.
This presentation reviewed research results within an emerging area of application security: the human dimensions that relate to secure code development. These findings were first publicly presented at AppSecUSA 2018.
Secure Decisions has built a comprehensive portfolio of R&D and commercially available software tools for application security. In addition to our Application Security Technology and Metrics (ASTAM) research program, we are actively working in other areas, like those below.
Code Ray
Hybrid Analysis Mapping
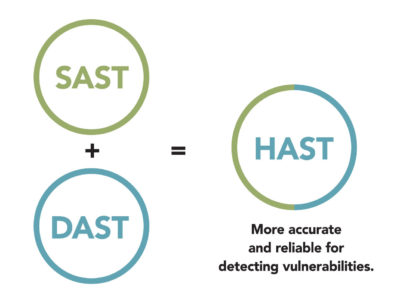
Two methods for analyzing software security risks are dynamic application security testing (DAST), an outside-in perspective, and static application security testing (SAST), an inside-out perspective. Both have shortfalls. DAST findings do not give insight into the root cause, making remediation time-consuming. SAST tools give you full breadth, but warn of weaknesses that are not exploitable.
Correlating the results of SAST and DAST can overcome these individual challenges. Secure Decisions is currently engaged in a DHS-funded Phase II SBIR program entitled Code Ray: Software Assurance Risk Management Framework for Hybrid Analysis Mapping, to produce a hybrid analysis method that can be incorporated into Code Dx and into the DHS SWAMP.
The anticipated end result of this R&D program will (1) improve speed, accuracy and confidence in detection of vulnerabilities by cross-mapping and normalizing the output of hybrid techniques – dynamic analysis, dynamic tracing, static analysis, and static contextual analysis; (2) enhance prioritization and mitigation of vulnerabilities by providing both the run-time context for those vulnerabilities and their mapping to security standards; and (3) improve the rapid comprehension and assessment of risks associated with vulnerabilities by delivering results in a simplified risk-management framework. Please review our factsheet to learn more about Code Ray.
Code Dx
 Software Vulnerability Management System
Software Vulnerability Management System
Code Dx is a software suite that combines and correlates vulnerabilities discovered from separate application security testing tools and techniques. Originally begun as a Small Business Innovation Research project from Department of Homeland Security, Code Dx was first created to fill in the gaps left by using tools individually. Because each application security testing tool and technique only finds a relatively small subset of vulnerabilities, there was a dire need for a solution to ensure maximum attack surface coverage. Rather than attempt to provide an automated testing tool that can only focus on a few types of vulnerabilities, Secure Decisions designed Code Dx to integrate with a wide variety of other tools and techniques, and combine and correlate the results of each in a single, unified interface. Code Dx normalizes the results from multiple tools, techniques, and formats; the end result is a clear, concise view of specific vulnerabilities that are immediately actionable, which is immensely helpful to software security and quality assurance professionals.
After the research period was completed, Secure Decisions successfully transitioned the Code Dx software suite into a commercial product, and spun off a separate company, Code Dx, Inc. to continue support for it. For more information, visit CodeDx.com.
Code Pulse
 Penetration testing has proven to be a valuable preventive application security technique. A variety of automated tools and manual approaches are used to assess and expose vulnerabilities in target applications. By definition, black box testing offers little insight into the internals of target applications. Therefore, understanding the code coverage and testing overlap, or perhaps more importantly the coverage boundaries, has often been difficult to ascertain. Secure Decisions has built a free open source tool, Code Pulse, to help overcome these challenges. Code Pulse is a visualization-centric tool that provides insight into the real-time code coverage of black box testing activities. It is a desktop application that runs on most major platforms. Code Pulse is an OWASP project. For more information, please visit the Code Pulse OWASP Project page.
Penetration testing has proven to be a valuable preventive application security technique. A variety of automated tools and manual approaches are used to assess and expose vulnerabilities in target applications. By definition, black box testing offers little insight into the internals of target applications. Therefore, understanding the code coverage and testing overlap, or perhaps more importantly the coverage boundaries, has often been difficult to ascertain. Secure Decisions has built a free open source tool, Code Pulse, to help overcome these challenges. Code Pulse is a visualization-centric tool that provides insight into the real-time code coverage of black box testing activities. It is a desktop application that runs on most major platforms. Code Pulse is an OWASP project. For more information, please visit the Code Pulse OWASP Project page.
CWE-Vis
 Common Weakness Enumeration Visualization
Common Weakness Enumeration Visualization
CWE-Vis is a resource made available to the software assurance community to explore and learn about weaknesses in software. It provides visualizations and interactions with MITRE’s Common Weakness Enumeration (CWE), an international standard created to define a dictionary of software weaknesses. The CWE greatly facilitates the discussion and collaboration in efforts revolving around the always-present quest to improve software systems. CWE-Vis helps users familiarize themselves with the CWE through visual means. High-level CWE structures and detailed relationship graphs are displayed visually helping users gain a better and quicker understanding of the CWE. Powerful filtering and searching is made available to allow users to focus in on the details of how weaknesses can be manifested in source code and ways to avoid and fix them.
Software Assurance Marketplace (SWAMP)

The SWAMP is a forward-looking effort to improve the state of secure software development, particularly for open source projects. Developed by Morgridge and funded by DHS it is a relatively recent effort that will be offering its initial capability in early 2014.