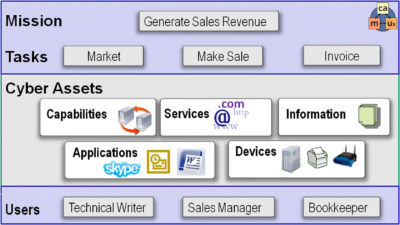
Systems administrators in large data centers often do not know the mission of the machines they manage; their strategy is, “Let’s pull the plug and see who calls.”
The problem is similar for computer security analysts – they do not know the cyber capabilities, mission, or users that depend on a machine that is attacked.
To assess the impact of a compromised or degraded cyber asset, analysts need to know:
- Who relies on an attacked asset for their job?
- What social network will be disrupted if an asset is compromised?
- What organizational mission is impacted by the loss of an asset?
- What other assets or cyber capabilities depend on an attacked asset?
- Where is the attacked asset located in the physical or logical network?
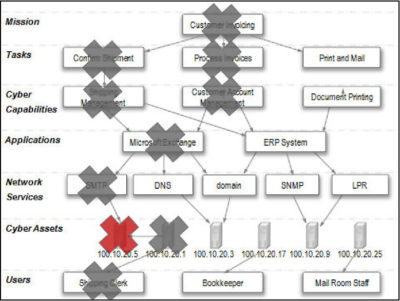
This lack of contextual information makes it impossible to effectively prioritize cyber events or assess the impact of attacks. Because organizations do not have accurate mappings between mission tasks and the network assets on which they depend, decision makers cannot accurately assess mission readiness of their network assets or interpret operational impact of network failures or cyber attacks. Security analysts cannot report operational impact of cyber incidents or defensive countermeasures. Managers are unable to accurately assess mission or business risks associated with cyber incidents, or identify cascading operational effects from the degradation or loss of cyber assets.
A current and accurately map of the dependencies between mission tasks, information needed to perform those tasks, and the cyber assets that provide and communicate that information.
Camus: Mapping Cyber Assets to Missions and Users