
MeerCAT®-Pro Wireless Security Visual Analytics
MeerCAT®-Pro is a visual analytics tool designed to help users locate wireless assets and networks, and assess the risks to their organization. Initially developed for and in close collaboration with the U.S. Department of Defense, MeerCAT® integrates data from wireless discovery and other security applications with a geographic information system (GIS) to provide a unified view of detected wireless devices, their vulnerabilities and threats.
Overview
Visual Tools for Wireless Security Analysis
MeerCAT® is a visual analytics tool designed to help users locate wireless assets and networks, and assess the risks to their organization. Initially developed for and in close collaboration with the U.S. Department of Defense, MeerCAT® integrates data from wireless discovery and other security applications with a geographic information system (GIS) to provide a unified view of detected wireless devices, their vulnerabilities and threats.
Many organizations that are unaware of the risks from/to wireless networks have an eye-opening experience by using MeerCAT® in conjunction with wireless data. It can be data you have collected by wardriving your organization’s campus, or data supplied with our demo.
What is the value of MeerCAT®?
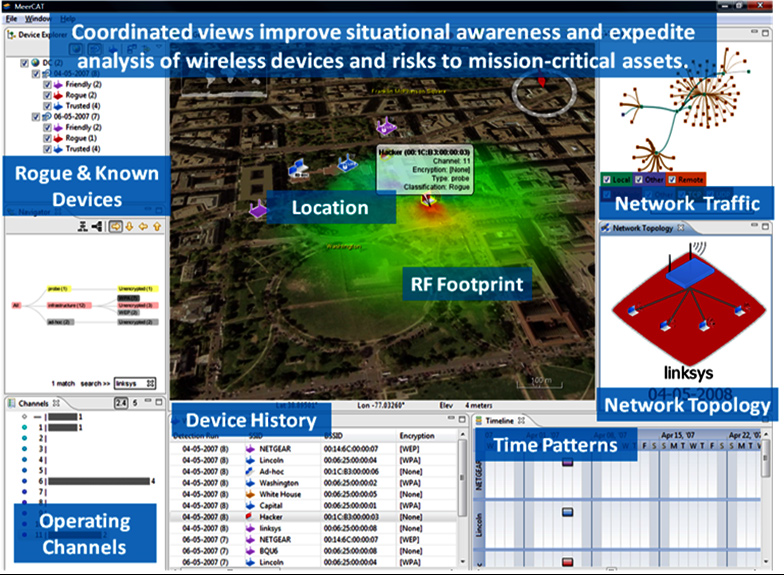
By visualizing wireless security information, MeerCAT® makes it easier for users to visually correlate large volumes of wireless data and see the wireless threats hidden in the haystack of data. MeerCAT® simplifies the analysis of wireless data for security and network professionals, and makes the information more accessible for those less skilled. The result is improved efficiency and accuracy in managing wireless security risks, reducing overall costs.
Award Winning Software

MeerCAT® is a Long Island Science and Technology Network (LISTNet) 2011 Long Island Software Award (LISA) Best Software Product winner.
It was recognized for excellence among Long Island-based software technology offerings.

MeerCAT® was a Government Security News (GSN) 2012 Homeland Security Awards Program Finalist in the category of Best Intrusion Detection/Prevention Solution. The GSN Homeland Security Awards Competition honors the partnership between all branches of the federal, state, and local and the private sector vendors of IT security and physical security products, solutions and technologies, whose combined efforts successfully defend and protect the nation’s people, property, and way of life.
Frequently Asked Questions
General Information
MeerCAT® auto-generates template-based and customizable reports to support regulatory compliance reporting. The generated reports provide visual snapshots and summaries of findings from wireless discovery, security audits and assessments. MeerCAT® reports and screenshots can be distributed via email and in various formats including Microsoft Office Word and PowerPoint. Information available in the visual reports include:
- Network topology maps
- Wireless network flow graphs
- RF channel usage and heatmaps
- Summary of intrusion detection alerts
- Inventory and location of discovered wireless
- Rogue devices
- Poorly secured devices
- Changed devices from a previous audit
Data-related
MeerCAT® currently supports the importation and analysis of a wide range of collection data formats:
- Wireless discovery (including Kismet and Flying Squirrel)
- Packet capture (including AirPcap, libpcap, and Wireshark)
- Intrusion detection (including Snort, and Aruba RFprotect)
Secure Decisions will interface MeerCAT® functionality to other data sources to meet the needs of our users and of our users and the wireless security community. For a most up to date list of supported tools or custom development for specific applications, contact us at (631) 759-3988.
Users
MeerCAT® is a government-sponsored software application developed in close collaboration with government and commercial security professionals who use wireless discovery and intrusion detection systems. Users include:
- Operational security personnel, computer network defenders and penetration testers responsible for intrusion detection
- Security professionals who conduct periodic wireless security audits for regulatory and policy compliance
- Network administrators responsible for WLAN asset tracking and management
Availability & Editions
System Requirements
No special hardware is needed to run MeerCAT® other than a typical PC (desktop or laptop). We currently recommend the following minimum system requirements to run MeerCAT® and a GIS to view the location of wireless devices and their RF signal footprint discovered from an outdoor (e.g., campus or city-wide) audit.
- Intel Pentium 3 (1 GHz) or AMD Athlon, or higher
- 256 MB of RAM
- 3D graphics card
- 1 GB disk space
Organizations that would like to use ArcGIS as the GIS platform or Microsoft Virtual Earth can reach us at(631) 759-3988 or through our contact page for further information.


